In the old days, stealing valuable information from a competitor in the industry involved steps found only in action movies. Corporate espionage meant planting a mole in a competing plant, torturing an employee to give up information, or opening a physical lock and key where documents are kept. These days, everything is digital. Whatever a perpetrator needs can be stolen with a few taps on an Internet-connected device.
Data breaches have long been a problem for many organizations due to the gravity of the consequences that follow. Nearly 9 out of 10 large organizations surveyed in the United Kingdom suffered from a security breach. These days, organizations that get breached would need to deal with the potential drops in stock values, issues arising from affected customers, legal liabilities, and the process of finding out the details around the breach.
When Sony Pictures Entertainment was hacked in 2014, as much as 100 terabytes of data was said to be stolen by a hacker group. This caused the leak of sensitive data like network user names and passwords, employee names and salaries, performance reviews, Hollywood stars’ passport and visa details, and many other personally identifiable information. The company also had to stop operations for a time to get its network back on its feet.
Did you know that this type of situation can actually arise from daily employee habits? These are the ones that are NSFW (not safe for work):
Opening and Replying to Messages from Internet Strangers
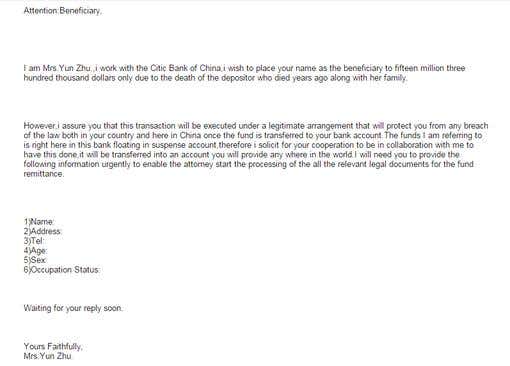
Few people are likely to reply to this spammed message from an Internet stranger, or so we might think. Sometimes, untrained and targeted individuals may just be trusting enough to indulge the stranger for an initial back and forth, unknowingly opening up his or her mailbox or social media inbox to a cybercriminal who may use certain social or technical tricks to get more information. Keep Internet strangers at bay.
Downloading Personal Files Using the Company Network

Source: Malwarebytes Blog
Sometimes, employees tend to use the corporate network for personal concerns, such as downloading software, printing personal files, or downloading bootlegged or illegal files. Network sharing and torrent sites are known disease vectors that could potentially allow malware to get into corporate systems.
Cartoonishly Crazy Password Practices

Gone are the days when everyone thinks it clever and cool to use “password” as a password, because, who would have thought, right? You should know that it's the second most popular password in the world, right after “123456.” Employees who use passwords found on this list and in dictionaries, or those who use combinations from their birthdays are liable to get their work accounts hacked by cybercriminals.
Putting Backups in the Back Burner
In 2012, Wired writer Mat Honan’s Google and Apple accounts were hacked and wiped clean. His Apple ID account contained what he described as “more than a year’s worth of photos, covering the entire lifespan of my daughter, or documents and e-mails that I had stored in no other location.” Backing up his Macbook could have saved those files in a device other than his Apple account. This should also apply to corporate files to make sure that operations will not slow down in case of data loss or a breach. Employees need to follow the 3-2-1 backup rule, which calls for three copies of important files in two different formats and with one copy off-site.
Saving Company Data on Device, and Losing Said Device
A recent study on data breaches revealed that roughly 4 in 10 breaches are caused by a lost device. Lost devices can be a goldmine for strangers who may be motivated enough to try and pry open even password-protected mobile or laptop devices to get information. Many data leaks were caused by lost laptops with corporate data stored in them. It is especially problematic for mobile devices as there are more instances by which employees are more likely to lose them and the data in them.
(Unknowingly) Clicking on Malicious Links

Source: zeltser.com
Although many causes of data breaches may be hard to trace and details of investigations are largely kept hidden, security researchers agree that similar hacks done before may start with something as small as an email with a link that downloads malware to spy on computers. Employees may unknowingly click on what they think were safe links but end up downloading malware. Keeping anti-malware solutions on systems can help catch malware before they are downloaded.